Table of Contents
- The benefits of AppLocker
- Using AaronLocker to make AppLocker easier
- Setup and configuration
- Hypothesis and results
- Conclusion
With the rising threats of cyberattacks, many organizations are taking proactive steps to secure their IT environments and reduce their attack surfaces. One method for improving security is application allowlisting, also known as whitelisting, such as Microsoft AppLocker. But how does it affect system performance? This research will explore the use and performance impact of Microsoft AppLocker.
Source: Gartner.com
The benefits of AppLocker
Microsoft AppLocker is a built-in security feature for Windows Operating Systems, designed to enforce application allowlisting, enabling only pre-approved software to run on the operating system. By allowing specific executables, Windows Installers, scripts, and packaged applications, AppLocker effectively prevents the execution of non-approved and potentially malicious software. Based on our experience, it has demonstrated strong protection against malware during numerous penetration tests conducted across various customer environments.
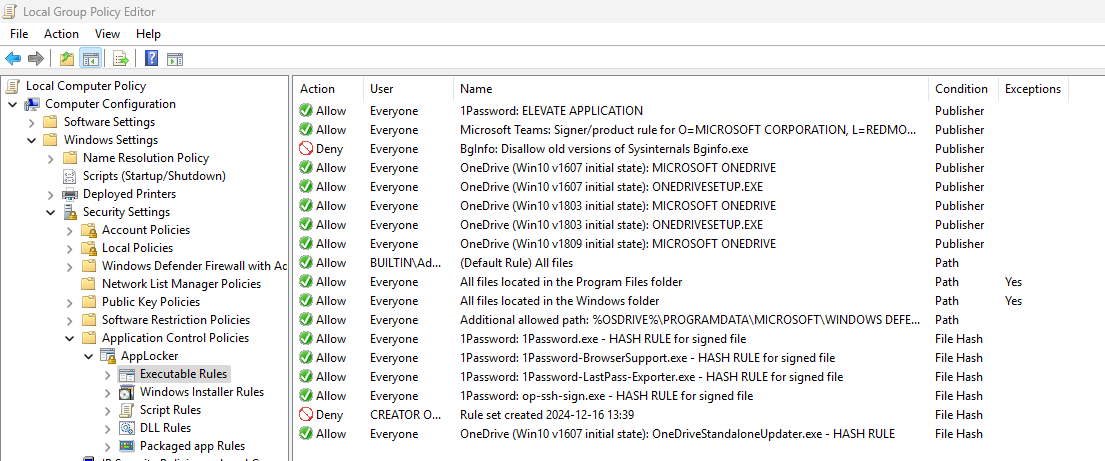
However, its management can be a hassle, mainly when dealing with individual rules. Each application or executable requires its own rule, which quickly becomes a tedious and time-consuming process, especially in dynamic environments where software is frequently updated or changed.
Administrators must manually add and adjust rules to ensure compliance, which can lead to potential gaps in security if overlooked. Additionally, maintaining these rules requires an in-depth understanding of the applications in use and regular audits to keep the policy up to date.
While AppLocker offers robust protection, it demands a high effort to manage effectively. Organizations may benefit from exploring automation tools or complementary solutions to streamline this process and reduce the administrative burden.
For further details about Microsoft AppLocker, visit the Microsoft site.
Using AaronLocker to make AppLocker easier
Effective application allowlisting relies on the proper configuration of allow rules. Poorly implemented rules, especially those permitting access to user-writable folders, can create security vulnerabilities. Hackers can exploit these vulnerabilities to bypass AppLocker protection and execute malicious software.
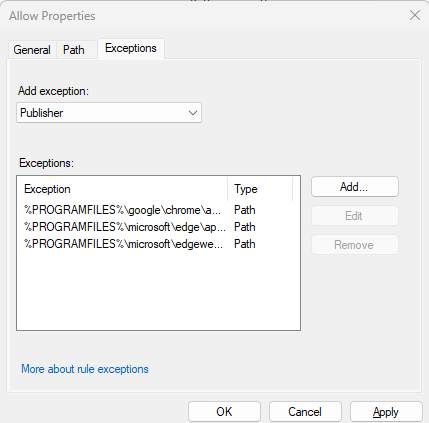
AaronLocker simplifies and enhances the implementation of AppLocker by automating the creation and management of allowlisting. This reduces the risk of human error in manual configurations. This scripted approach allows organizations to set up application allowlisting in just a few hours. However, it is important to note that AaronLocker does not attempt to restrict administrative users from executing any application or script.
Designed to streamline the process, AaronLocker helps organizations create and maintain strict, robust application control policies for both AppLocker and Windows Defender Application Control (WDAC). This research focuses exclusively on AppLocker and does not include an in-depth analysis of Windows Defender Application Control (WDAC). To understand the difference between AppLocker and WDAC, you are recommended to read the following Microsoft page. AaronLocker consists of a minimal set of PowerShell scripts, allowing easy rules customization through straightforward text-file edits. For more details, visit the AaronLocker GitHub repository.
Setup and configuration
As the introduction outlines, this research aims to evaluate the overall impact of implementing Microsoft AppLocker on performance. A detailed analysis of the effects on application startup times and the frequency of scans is outside the scope of this research and will be addressed in a follow-up research.
As with most research, this is executed within a Virtual Desktop Infrastructure (VDI) environment. The AppLocker configurations are applied to the VDI environment using rules generated by AaronLocker and enforced via Group Policies on the targeted virtual desktops. The AppLocker configuration is running in Enforced mode, which includes DLL scanning. This research contains two scenarios:
- AppLocker not configured (disabled)
- AppLocker configured (enabled)
The virtual desktops run Windows 10 22H2, as this is a commonly used Windows edition in enterprise environments, and are delivered through Citrix Virtual Apps and Desktops 2402 LTSR. Each virtual machine is provisioned with 4 vCPUs and 8 GB of memory. To simulate a realistic user load, LoadGen is applied in combination with the default GO-EUC workload.
The following applications are started during the simulation:
- Microsoft Outlook
- Microsoft Word
- Microsoft Excel
- Microsoft PowerPoint
- Adobe Reader DC
- Microsoft Edge
A total of 32 VDIs are deployed, intentionally underutilizing the underlying system resources. This approach ensures that the comparison focuses on the performance differences between the two scenarios rather than the impact of system saturation.
For further details regarding the workload simulation in this research, please refer to the GO-EUC testing methodology.
Hypothesis and results
Implementing an application allowlisting solution like Microsoft AppLocker introduces an application access control list (ACL). This ACL is checked every time the operating system attempts to execute an executable DLL, script, Windows Installer, or Windows package, determining whether the action is permitted. The hypothesis is that this continuous evaluation might impact overall system performance.
While research data is collected from both the hypervisor and VM levels, let’s first start from the VM perspective.
The CPU load on a VM level is similar between the two scenarios, showing no direct CPU impact.
The pattern between the two scenarios also applies to the memory usage in the VM, showing a small difference.
Disk activity, measured in reads/sec and writes/sec, shows a slight variation between the two scenarios. In this instance, the AppLocker enabled scenario showed marginally lower activity. However, in another VM, the opposite was observed. These differences are minimal and unlikely to be noticeable from a user perspective.
Let’s change the perspective to the hypervisor level. As described in the configuration, this research hosts 32 VDIs in total.
When comparing hypervisor CPU Usage between the two scenarios, a very slight increase (almost nihil) is observed when AppLocker is enforced. This increase is negligible, suggesting a minimal impact on CPU performance.
Overall, the metrics from a VM level reflect on the hypervisor, showing a slight increase in disk activity, but on this scale, the impact will be unnoticeable from a user perspective.
Conclusion
Cyber threats continue to rise, and protecting your organization from attacks is important. Microsoft AppLocker is an effective tool for enhancing security by restricting which programs and applications are allowed to run, thereby reducing the attack surface. This can be applied to physical Windows-based devices and virtual desktops delivered via Microsoft Azure Virtual Desktop, Microsoft Windows 365, Citrix Virtual Apps and Desktops, and Omnissa Horizon.
This research compares AppLocker in disabled and enabled modes (with DLL scanning) and observes a minimal performance impact. It’s important to note that the load test used a limited subset of applications, which differs from a real-world environment. Given the minimal load increase observed during the test, it’s expected that adding more rules to AppLocker might result in a noticeable increase in performance. However, it is always recommended that you validate this in your context.
Based on our experience with various customers, penetration tests have confirmed that the combination of Microsoft AppLocker, managed by AaronLocker, provides strong protection against attacks. Additionally, integrating SIEM tools like Microsoft Sentinel to monitor AppLocker events can help detect suspicious activity, such as the rapid execution of blocked scripts, which may indicate a potential security threat.
Before implementing AppLocker into production, it is essential to have clear procedures for onboarding new applications. There is a high chance that users will experience applications not working as expected, as they could be blocked. Therefore, having clear user-oriented instructions on how to indicate AppLocker behavior and how to submit a request is a crucial part of making your AppLocker implementation a success.